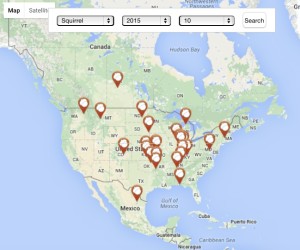
While surfing today, I came across this article about showing a world map and the various successful confirmed attacks against the USA power grid. The media might have you believing that cyber terrorism is an important threat vector. Maybe in the future it will be, but according to this data, looks like squirrel attacks are […]