VMware’s vCenter server has some build-in alarms and alerting functionality. But, sometimes, a production environment wants to integrate with an existing solution or use a more comprehensive solution that also alerts when problems happen with physical servers. In any case, you might need the new solution to query the VMware environment, which is best achieved with a new read-only user account.
This blog details the steps of creating a read-only user in VMware. In a completely different scenario, you might also want to create such a user if you are doing an audit or performance evaluation, and don’t want to give the consultant working the audit the rights to alter settings.
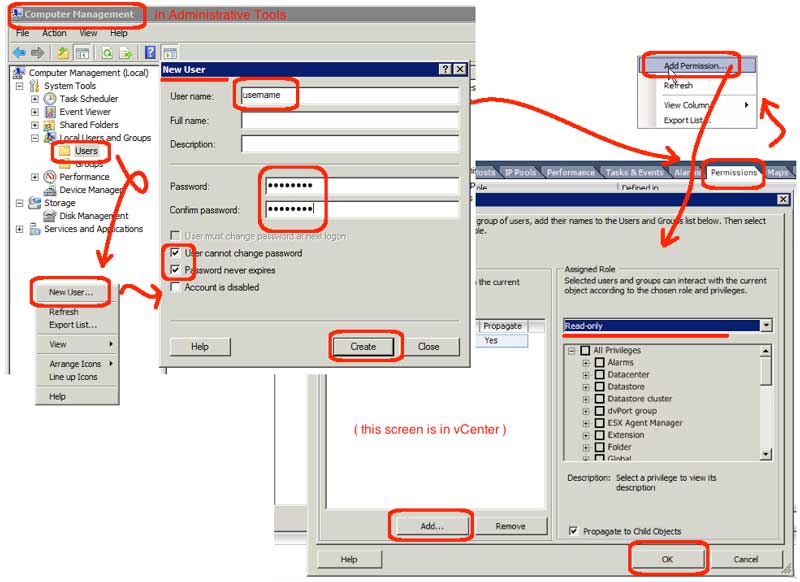
- Create a local user account on the vCenter server:
- Open Administrative Tools | Computer Management
- Expand Local Users and Groups | Users
- Right-click and select the “New User” menu item
- Enter the username (note: don’t embed spaces)
- Optionally, enter the full name and description
- Enter the initial password and confirm the initial password
- If this is a service account, uncheck the “User must change password” checkbox
- If this is a service account, check the “User cannot change password” checkbox
- If this is a service account, check the “Password never expires” checkbox
- Click the Create button
- Click the Close button and exit Computer Management
- Assign the local user rights in vCenter:
- Login to the vSphere client (with administrative rights)
- Highlight the data center name
- Goto the Permissions tab
- Right-click and select the “Add Permission” menu item
- Click the Add button
- Highlight the user you want to add
(Note: interface defaults to showing you local users, but you can also give domain users rights) - Click the Add button and then the OK button
- Validate the rights say “Read-Only” and click the OK button
- Test your new user:
- Logout of the vSphere client
- Open the vSphere client and uncheck the “Use Windows session credentials”
- Enter the username and password that you just created
- Click the Login button
- Go back to the Permissions tab…
- Right-click and look for the “Add Permission” menu item — it should be greyed out since you entered as read-only
Personally, I prefer to make service account local accounts on the specific machine on which they need access. This prevents someone from mis-using a service account as a domain user login on machines that are unrelated to the service. But, in some environments, security policies prevent the creation of local user accounts, and prefer domain accounts. Either will work.