So, today I wanted to forward VMware ESXi host syslog data to my newly installed Splunk server. “No problem,” I thought to myself. But, strangely, my changes did not result in any actual data being collected. It turns out that the VMware firewall blocks outbound syslog by default, and so I had to change its settings, too.
Here are the detailed steps for setting up VMware syslog forwarding success using VMware 5.1 and the iSphere client:
- Enable Syslog Forwarding:
- Login to the iSphere client
- Highlight the VMware ESXi host
- Click the Configuration tab
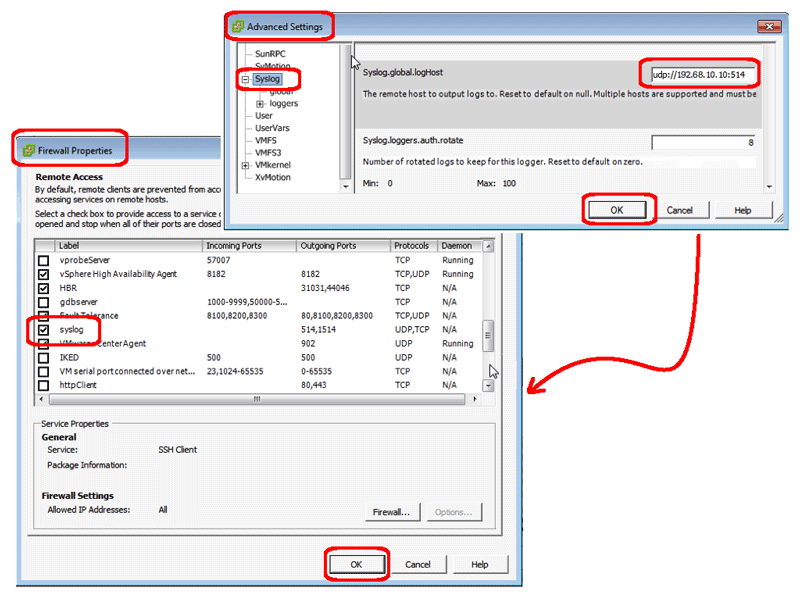
- In the Software Box | Click Advanced Settings
- Click Syslog in the tree
- Scroll to the “Syslog.global.logHost” field and enter udp://hostname:514
(Note: you can use either the hostname or the IP address of your syslog server) - Click the OK button
- Allow Syslog Through Firewall:
- Staying in the Configuration tab of the ESXi host…
- In the Software Box | Click Security Profile
- Beside the Firewall label, click the Properties link
- In the “Firewall Properties” dialog box, scroll down to syslog
- Check the syslog checkbox, to allow it through the firewall
- Click the OK button
Syslog data appeared immediately, and I did not need to reboot the host. Problem solved!